J
Jarret W. Buse
Guest
NMAP PING and UDP Scanning
When using NMAP, there are basic scans which are used to find specific information. These scans are the most used by NMAP and can be handy depending on what you need to discover on a system or a network.
Let's start by listing the basic scans. The four basic scans are:
This article covers the first two scans: PING and UDP.
The PING Scan is used to find online systems. With any NMAP scan, the local subnet or remote subnet can be scanned. The PING Scan is a fast scan since it does not check for open Ports, but only if the system with the IP Address is available. The PING frames can appear common on a network if viewed with a packet sniffer. The PING Scan does not require Root privileges when used with NMAP. Keep in mind that the PING Scan only allows an inventory listing of systems with no Port information.
Each query for a Ping Scan could only produce two frames. One frame, an ICMP ECHO Request, is sent to have a system respond if it has the matching IP Address. If the system is on, it will respond with an ICMP ECHO Reply.
Let's look at a sample Ping Scan. The command is “nmap -sP <ip address>”.
In my example, I will show a basic PING Scan of the local subnet “10.0.0.0/24”. On this local subnet there are only two systems. The one system is running NMAP and Wireshark while the other is a Windows XP SP3 system called “Dell”. The output for NMAP is shown in Figure 1. The Wireshark output for the scan is shown in Figure 2.
NOTE: Wireshark is a network packet sniffer found at www.wireshark.org.
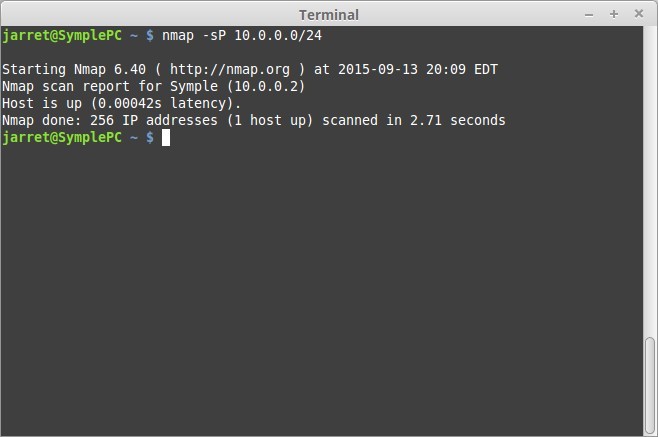
FIGURE 1
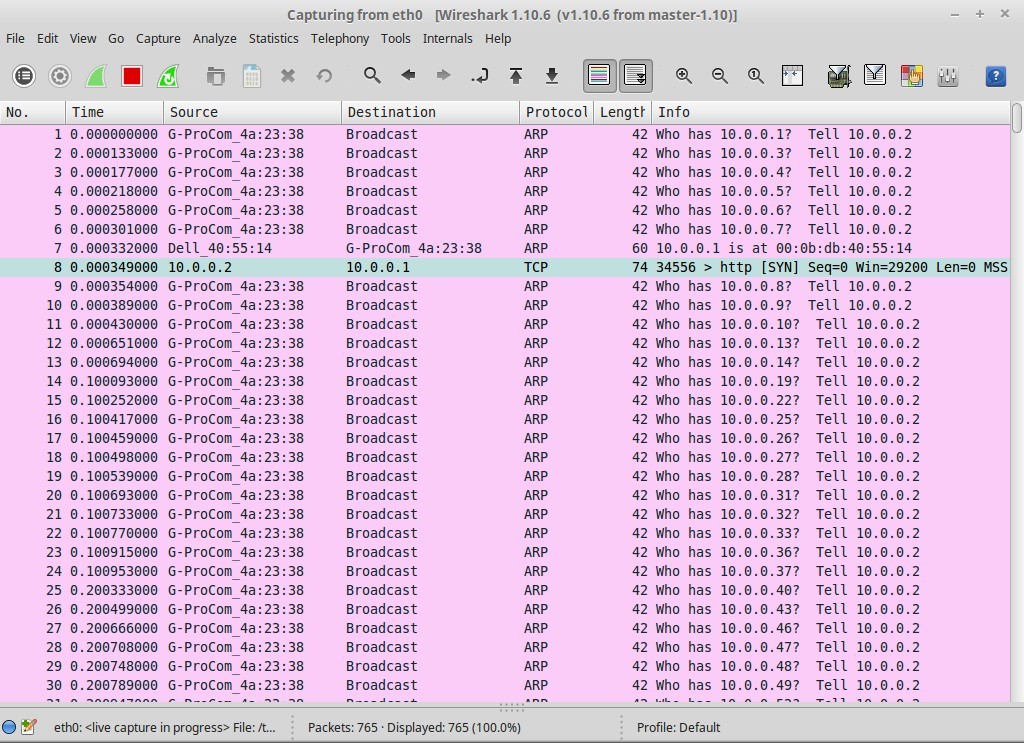
FIGURE 2
The total number of frames captured is 765. The first page, shown in Figure 2, details the main portion of finding the one system.
In Figure 2, the “pink” lines show the Address Resolution Prototol (ARP) requests made to find the system with the specified IP Address. You may notice that IP Address “10.0.0.2” was skipped since it is the address of the local system.
Many Broadcasts are sent out for each IP Address in the specified subnet (10.0.0.0/24). To be safe that packets are not lost, each IP Address is sent a request a total of three times.
The Pink row, Line 7 in Figure 2, shows the ARP Response from the system with the IP Address 10.0.0.1. Line 8 shows it is sending a SYN request to the NMAP system, which is ignored.
Since the only ARP Response is from the system with IP Address 10.0.0.1, NMAP lists it in Figure 1. NMAP does not show the MAC Address, but it is listed in the details of the frame on Wireshark.
Now for the User Datagram Protocol (UDP) scan. The UDP scan is very essential for Network Administrators to perform. Most malware/spyware on systems which access the Internet use a UDP Port. UDP Ports are not usually monitored because few systems use UDP. Once a UDP Port is opened, the malware is placed on the system through the opened port. Once on the system, the malware can cause a system failure of the Operating System (OS). Spyware on a system can open a UDP Port and transmit personal information from the local system to an Internet system.
The UDP Scan checks for online systems on which open/filtered UDP Ports are available on a system. There is no handshake for UDP since it is connectionless-oriented. The scan does require that the NMAP application have Root privileges. A UDP Scan can cause numerous frames on the network. With NMAP, the UDP Scan is the only way to scan UDP Ports.
Each query for a UDP Scan should only produce, at most, two frames. One frame specifies an UDP and Port Number that is sent to the specified system on the designated UDP Port number. If the system is on and has an open Port, it will respond with the second frame which is an UDP and Port Number data response. If the Port is closed, it may respond with an “ICMP Port Unreachable” message. It is possible that no response will signify the Port is closed.
Let's look at a sample UDP Scan. The command is “sudo nmap -sU <ip address>”.
NOTE: The top 1,000 well known UDP Ports are scanned, so the scan may take some time.
To run a scan on the same network as performed with the previous PING Scan, the command would be “sudo nmap -sU 10.0.0.0/24”.
The output for NMAP is shown in Figure 3. The Wireshark output for the scan is shown in Figure 4.
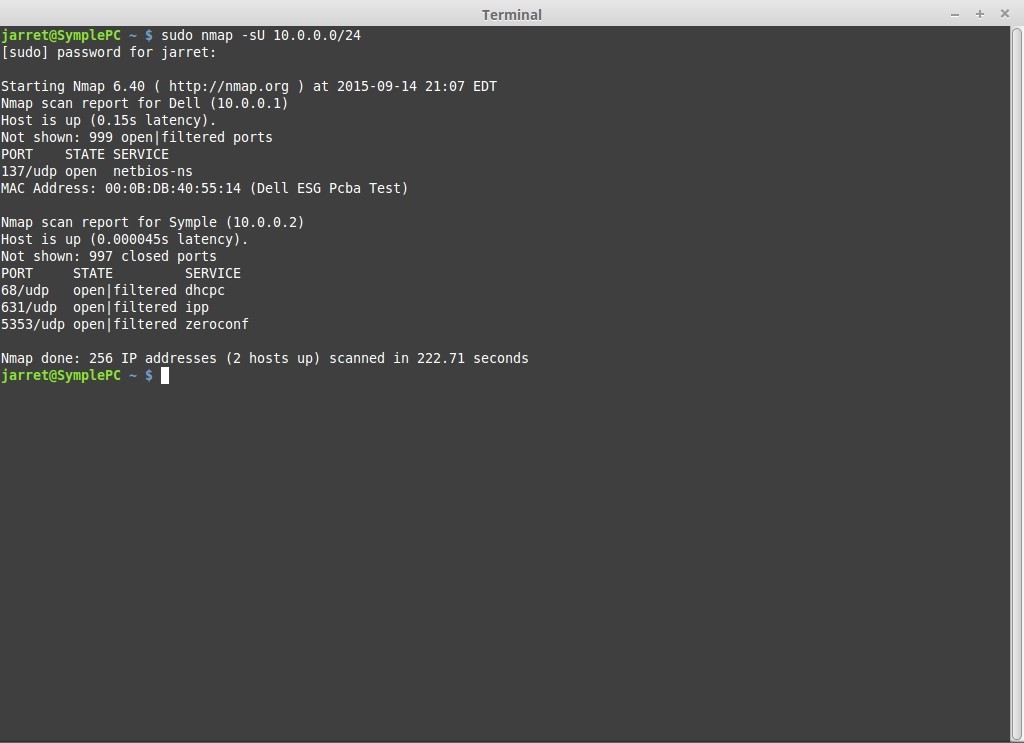
FIGURE 3
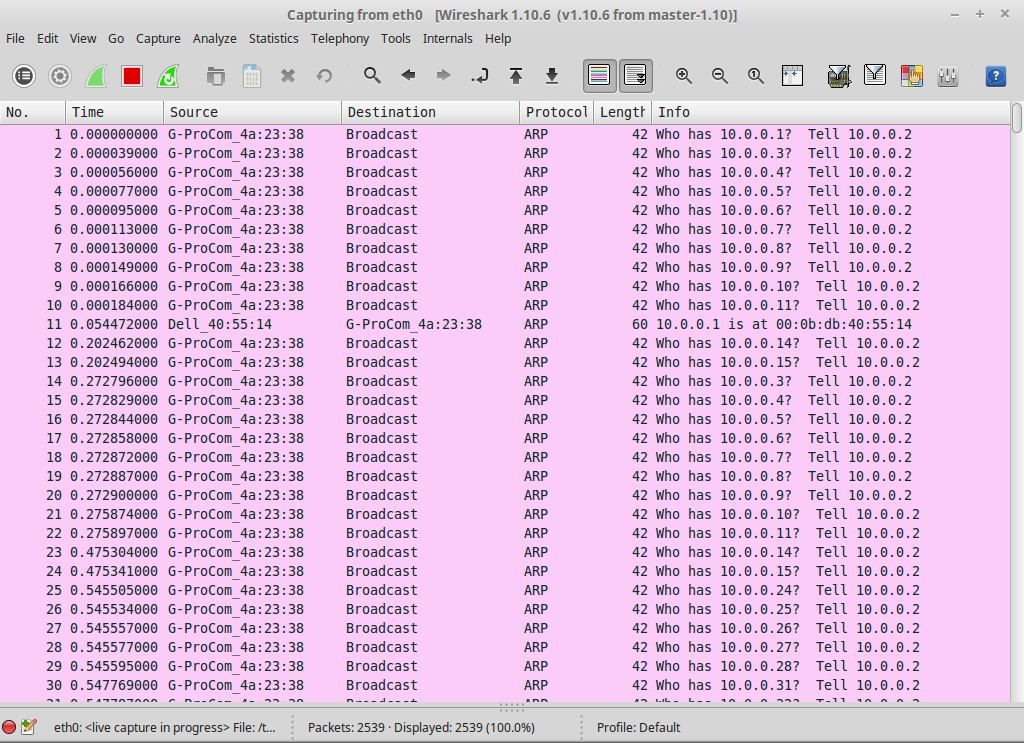
FIGURE 4
The total number of frames captured is over 1,000. The first page, shown in Figure 4, details the main portion of finding the one system.
In Figure 3 you can see the first system, the Dell, shows Port 137 is open. The well-known UDP port is used for “netbios-ns”.
In Figure 5 you can see that there were numerous responses for the NBNS Protocol. These are the responses for the open port at Port 137.
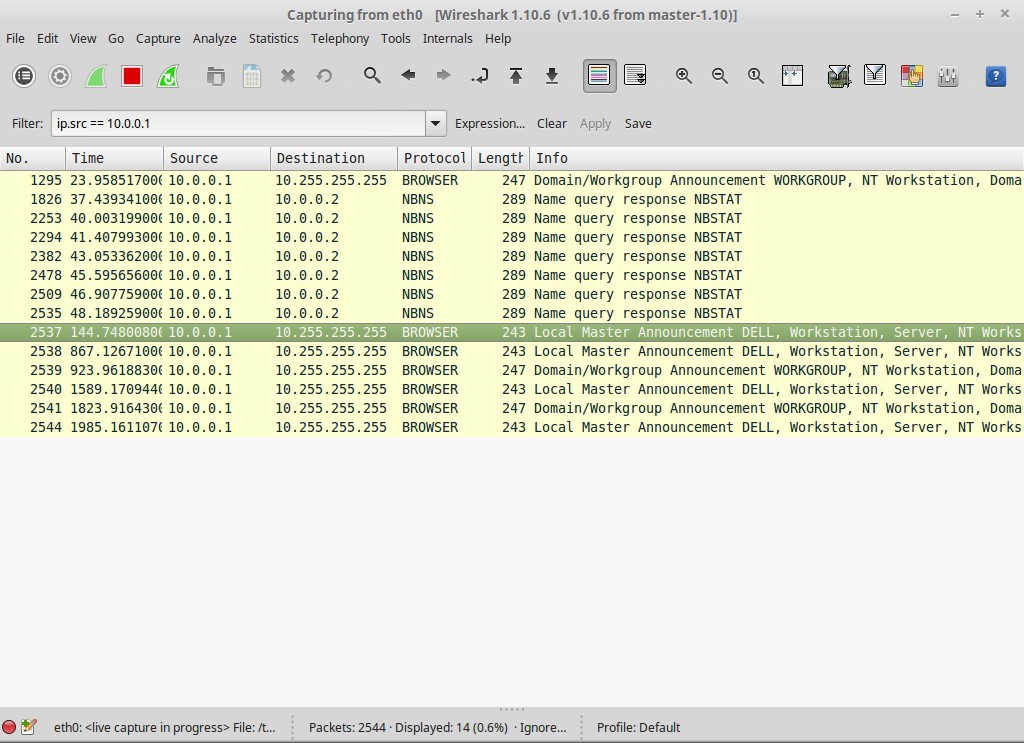
FIGURE 5
Since the scan is for UDP and it is connectionless, this is why there are so many frames being sent. The UDP Protocol does not support guaranteed delivery of all packets. If a packet is lost, then the Source Host will not be notified to resend the missing packets. Since there is no guarantee, all packets need to be sent multiple times.
Try these two scans and see how they work on your subnet or even the Internet.
When using NMAP, there are basic scans which are used to find specific information. These scans are the most used by NMAP and can be handy depending on what you need to discover on a system or a network.
Let's start by listing the basic scans. The four basic scans are:
- PING Scan (-sP)
- UDP Scan (-sU)
- TCP SYN Scan (-sS)
- TCP Connect Scan (-sT)
This article covers the first two scans: PING and UDP.
The PING Scan is used to find online systems. With any NMAP scan, the local subnet or remote subnet can be scanned. The PING Scan is a fast scan since it does not check for open Ports, but only if the system with the IP Address is available. The PING frames can appear common on a network if viewed with a packet sniffer. The PING Scan does not require Root privileges when used with NMAP. Keep in mind that the PING Scan only allows an inventory listing of systems with no Port information.
Each query for a Ping Scan could only produce two frames. One frame, an ICMP ECHO Request, is sent to have a system respond if it has the matching IP Address. If the system is on, it will respond with an ICMP ECHO Reply.
Let's look at a sample Ping Scan. The command is “nmap -sP <ip address>”.
In my example, I will show a basic PING Scan of the local subnet “10.0.0.0/24”. On this local subnet there are only two systems. The one system is running NMAP and Wireshark while the other is a Windows XP SP3 system called “Dell”. The output for NMAP is shown in Figure 1. The Wireshark output for the scan is shown in Figure 2.
NOTE: Wireshark is a network packet sniffer found at www.wireshark.org.
FIGURE 1
FIGURE 2
The total number of frames captured is 765. The first page, shown in Figure 2, details the main portion of finding the one system.
In Figure 2, the “pink” lines show the Address Resolution Prototol (ARP) requests made to find the system with the specified IP Address. You may notice that IP Address “10.0.0.2” was skipped since it is the address of the local system.
Many Broadcasts are sent out for each IP Address in the specified subnet (10.0.0.0/24). To be safe that packets are not lost, each IP Address is sent a request a total of three times.
The Pink row, Line 7 in Figure 2, shows the ARP Response from the system with the IP Address 10.0.0.1. Line 8 shows it is sending a SYN request to the NMAP system, which is ignored.
Since the only ARP Response is from the system with IP Address 10.0.0.1, NMAP lists it in Figure 1. NMAP does not show the MAC Address, but it is listed in the details of the frame on Wireshark.
Now for the User Datagram Protocol (UDP) scan. The UDP scan is very essential for Network Administrators to perform. Most malware/spyware on systems which access the Internet use a UDP Port. UDP Ports are not usually monitored because few systems use UDP. Once a UDP Port is opened, the malware is placed on the system through the opened port. Once on the system, the malware can cause a system failure of the Operating System (OS). Spyware on a system can open a UDP Port and transmit personal information from the local system to an Internet system.
The UDP Scan checks for online systems on which open/filtered UDP Ports are available on a system. There is no handshake for UDP since it is connectionless-oriented. The scan does require that the NMAP application have Root privileges. A UDP Scan can cause numerous frames on the network. With NMAP, the UDP Scan is the only way to scan UDP Ports.
Each query for a UDP Scan should only produce, at most, two frames. One frame specifies an UDP and Port Number that is sent to the specified system on the designated UDP Port number. If the system is on and has an open Port, it will respond with the second frame which is an UDP and Port Number data response. If the Port is closed, it may respond with an “ICMP Port Unreachable” message. It is possible that no response will signify the Port is closed.
Let's look at a sample UDP Scan. The command is “sudo nmap -sU <ip address>”.
NOTE: The top 1,000 well known UDP Ports are scanned, so the scan may take some time.
To run a scan on the same network as performed with the previous PING Scan, the command would be “sudo nmap -sU 10.0.0.0/24”.
The output for NMAP is shown in Figure 3. The Wireshark output for the scan is shown in Figure 4.
FIGURE 3
FIGURE 4
The total number of frames captured is over 1,000. The first page, shown in Figure 4, details the main portion of finding the one system.
In Figure 3 you can see the first system, the Dell, shows Port 137 is open. The well-known UDP port is used for “netbios-ns”.
In Figure 5 you can see that there were numerous responses for the NBNS Protocol. These are the responses for the open port at Port 137.
FIGURE 5
Since the scan is for UDP and it is connectionless, this is why there are so many frames being sent. The UDP Protocol does not support guaranteed delivery of all packets. If a packet is lost, then the Source Host will not be notified to resend the missing packets. Since there is no guarantee, all packets need to be sent multiple times.
Try these two scans and see how they work on your subnet or even the Internet.


