SELinux stands for Security Enhanced Linux. Security is enabled that causes security to lock down access to the system. SELinux is a Mandatory Access Control (MAC) which is part of the Kernel to limit resources for programs, this includes access by clients.
There are two active modes in SELinux, one is to strictly enforce the security and to lock down the system. The other mode will allow access, but log the 'intrusion'.
Modes
The default mode for SELinux on CentOS 7 is 'Enforcing' mode. This lock-downs the system and prevents security from being broken, while also logging the attempt.
For Ubuntu, the default SELinux mode is 'Permissive'. For Ubuntu, SELinux is not installed, but the system does not enforce SELinux security but does log attempts.
The last mode is 'Disabled'. Of course, there is no enforcement or logging.
To determine your mode, use the command 'getenforce'.
Installing SELinux
For Ubuntu and CentOS, we need to install more packages.
In Ubuntu, we need to stop and disable AppArmor with the following commands:
sudo systemctl stop apparmor
sudo systemctl disable apparmor
For Ubuntu, we need the following:
sudo apt install policycoreutils
sudo apt install selinux selinux-utils selinux-basics auditd audispd-plugins smbclient
During the installation, you will be asked to reboot the system when the installation is completed.
This installs the main packages needed for managing SELinux.
sudo apt install setools
The 'setools' package lets you manage the policies for SELinux.
For CentOS 7 we need similar packages. To find the current package, use the command 'sudo yum whatprovides semanage'. The output should be similar to Figure 1. You need to look for the one that is for '/sbin/semanage'. All the package names should be the same anyway. Copy the package name, or type it in to install.
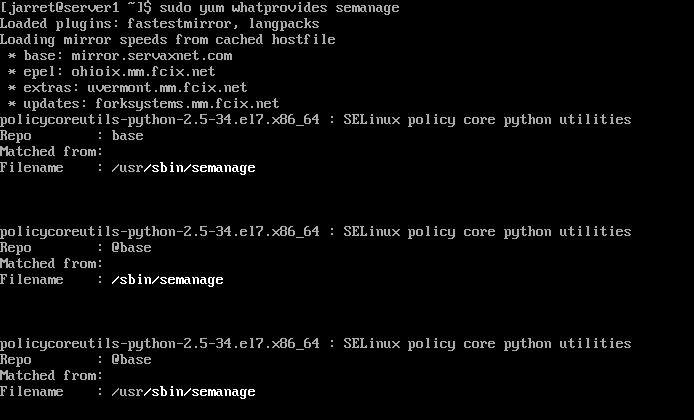
FIGURE 1
The following is an example:
sudo yum install policycoreutils-python-2.5-34.el7.x86_64
These are the packages for managing SELinux on CentOS.
Next, we need to install the files necessary to manage the SELinux policies:
sudo yum install setools-console
For either Operating System, we can run the command 'sudo sestatus'. It should show that SELinux is enabled.
Now that we have all the packages for SELinux, we need to install something to test SELinux security. Let's install Samba since it seems to be quite common so you can share files.
Samba Installation
For CentOS, it is simply the command:
sudo yum install samba samba-client samba-common
If you are using Ubuntu, execute the command:
sudo apt install samba samba-common
To check the status with 'systemctl', Ubuntu uses the service name 'smbd' and CentOS uses 'smb'. Perform the following to check on the status:
sudo systemctl status <service>
If the service is inactive, most likely on CentOS, then do the following:
sudo systemctl start <service>
sudo systemctl enable <service>
You can check the status again to verify the service is started.
Now that we can share files between systems, we need to create a shared folder. So, let's create a folder named 'linux'.
sudo mkdir /linux
If we look at the folder, we should see that the folder is owned by 'root' and has full access to the owner. The permissions for the group 'root' and everyone else is 'read' and 'execute'. We'll need to change these permissions. We need full permissions for all users as well as setting the Sticky Bit. The Stick Bit will allow the creator of files to delete their files, but no one else (except root users with elevated privileges).
sudo chmod 1777 /linux
The first '1' is the Sticky Bit'. The first '7' allows 'read', 'write', and 'execute' for the owner. The second '7' is for the groups that are set for the folder. The last '7' is for everyone else.
Switch into the new folder, 'cd /linux'. Use an editor, like 'vim' or 'nano', to create a file called 'test.txt'. Add some simple text to the file and save it. If you run the command 'ls -l', you should see something similar to Figure 2.
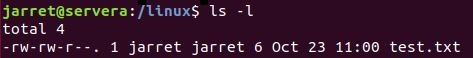
FIGURE 2
You can see in Figure 2 that I am the owner as well as my group has the ownership. So, my user and group can 'read' and 'write' to the file, but everyone else can only 'read'. Only my account can delete the file with 'write' permission.
We now have the folder set to share, we just need to get the folder into Samba so the service knows it exists and allows access to it.
Configure Samba
To add our folder to the share list, we need to edit '/etc/samba/smb.conf'. At the bottom of the configuration file, you can add new shares. The syntax is as follows:
[shared-name]
path=/path/to/shared/folder
writeable=yes
In our case, the section would be:
[share]
path=/linux
writeable=yes
In this case, the folder is '/linux' and the share name is 'share'. The two can be the same if you want it to be.
You can test the syntax of the 'smb.conf' file by running 'testparm'. You may notice that when it displays the line 'writeable=yes' as 'read only=no'. These lines are the same, but it does not change the line in the configuration file.
Now you need to restart the 'smb' or 'smbd' service using 'systemctl'.
sudo systemctl restart <service-name>
Under normal circumstances, no SELinux, this should be enough. Let's have a look at the share.
Samba Client
We need to set up a new user for Samba to allow the client to connect. We are also setting up the account on the local machine (Server1). The command is:
sudo smbpasswd -L -a <username>
So, on my system, I used the command:
sudo smbpasswd -L -a jarret
The parameter '-L' is for the local system and '-a' is to add a user.
You might be asked for the password to use 'sudo' and then for the command, you'll be asked to create a password and then retype it to verify that the two entries match.
To log into the system and connect to 'share', use the command 'smbclient //localhost/share'. It should ask you for the Samba password of the current user. If you want to log in as a different user, then use '--user=<username>'.
Once connected and logged in, you can use Samba commands at the 'smb: \>' prompt. You can use 'ls' and 'pwd' as you would in Linux.
NOTE: Everything should be working fine on Ubuntu since it defaults to permissive mode. You can change the default in the file '/etc/selinux/config'. On the line 'SELINUX=permissive', change it to 'SELINUX=enforcing', save the file, and restart the system. If you do, Samba will stop sharing the file. To make it work, you need to perform the same commands as in CentOS or leave it as 'permissive'. Setting Ubuntu as 'enforcing' can cause it not to work in VBox. To fix it, you need to go back into Recovery mode and edit the file, changing it back to 'permissive'.
So, let's assume that Ubuntu is in 'enforcing' mode like CentOS and we get an error using 'ls'. We can use 'pwd' to get the current folder name.
Since the folder will be a Samba share, we need to change the context type. If you run the command 'ls -dZ /linux' to see the directory (-d) and context (-Z) of the shared folder. The result is shown in Figure 3.

FIGURE 3
You should see the user is 'unconfined', the role is set to 'object_r', and the type is 'default_t'. We need to change the type to 'samba_share_t' so SELinux will recognize the folder as a Samba share. Use the following command to change the type on the share:
chcon -t samba_share_t /linux
You can run the 'ls -dZ /linux' command to see that the type has changed. If you use the 'restorecon' command, the type is set back to default and the share is lost.
If you connect to the smbclient, then you can run 'ls' and use the 'get' command to copy the file to the 'pwd' on your system. That is the 'pwd' before you run the 'smbclient' command'. The 'ls' command is shown in Figure 4.
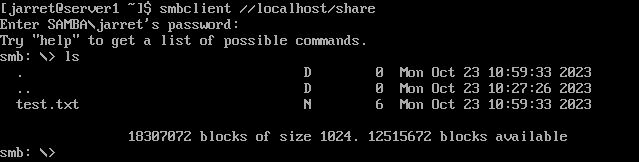
FIGURE 4
Permissive Service
If you run the command 'seinfo --permissive', the result is 'Permissive Types: 0'. We have no service set as Permissive.
We can use 'restorecon' to set the share back to 'default_t'. The command is 'sudo restorecon -Rv /linux'.
The Samba share should not be functioning again. So let's enable the Samba service as 'permissive'.
Use the command 'sudo semanage permissive -a smbd_t'. We specify 'smbd' as the service and '_t' as the type.
The SELinux policies should be recompiled after you issue the commands.
You can use 'ls' after connecting to the share and it should work.
Using the command 'seinfo --permissive' shows that there is one service and it is listed as 'smbd_t'.
Remote Connections
To allow connections to the local share from remote systems, you need to allow port access to TCP Port 445 and profile 'dns'.
sudo ufw allow dns
sudo ufw allow 445/tcp
On clients, you need to install the 'smbclient' for access from the command line. Otherwise, you can use 'nautilus' to open up the share from 'Other Locations' and then the Server and the share.
Conclusion
There was a bit of information here to set up security. Be sure to know this before you take the exam, if you do.
Try setting up SELinux with other services to make sure you understand the concept.
There are two active modes in SELinux, one is to strictly enforce the security and to lock down the system. The other mode will allow access, but log the 'intrusion'.
Modes
The default mode for SELinux on CentOS 7 is 'Enforcing' mode. This lock-downs the system and prevents security from being broken, while also logging the attempt.
For Ubuntu, the default SELinux mode is 'Permissive'. For Ubuntu, SELinux is not installed, but the system does not enforce SELinux security but does log attempts.
The last mode is 'Disabled'. Of course, there is no enforcement or logging.
To determine your mode, use the command 'getenforce'.
Installing SELinux
For Ubuntu and CentOS, we need to install more packages.
In Ubuntu, we need to stop and disable AppArmor with the following commands:
sudo systemctl stop apparmor
sudo systemctl disable apparmor
For Ubuntu, we need the following:
sudo apt install policycoreutils
sudo apt install selinux selinux-utils selinux-basics auditd audispd-plugins smbclient
During the installation, you will be asked to reboot the system when the installation is completed.
This installs the main packages needed for managing SELinux.
sudo apt install setools
The 'setools' package lets you manage the policies for SELinux.
For CentOS 7 we need similar packages. To find the current package, use the command 'sudo yum whatprovides semanage'. The output should be similar to Figure 1. You need to look for the one that is for '/sbin/semanage'. All the package names should be the same anyway. Copy the package name, or type it in to install.
FIGURE 1
The following is an example:
sudo yum install policycoreutils-python-2.5-34.el7.x86_64
These are the packages for managing SELinux on CentOS.
Next, we need to install the files necessary to manage the SELinux policies:
sudo yum install setools-console
For either Operating System, we can run the command 'sudo sestatus'. It should show that SELinux is enabled.
Now that we have all the packages for SELinux, we need to install something to test SELinux security. Let's install Samba since it seems to be quite common so you can share files.
Samba Installation
For CentOS, it is simply the command:
sudo yum install samba samba-client samba-common
If you are using Ubuntu, execute the command:
sudo apt install samba samba-common
To check the status with 'systemctl', Ubuntu uses the service name 'smbd' and CentOS uses 'smb'. Perform the following to check on the status:
sudo systemctl status <service>
If the service is inactive, most likely on CentOS, then do the following:
sudo systemctl start <service>
sudo systemctl enable <service>
You can check the status again to verify the service is started.
Now that we can share files between systems, we need to create a shared folder. So, let's create a folder named 'linux'.
sudo mkdir /linux
If we look at the folder, we should see that the folder is owned by 'root' and has full access to the owner. The permissions for the group 'root' and everyone else is 'read' and 'execute'. We'll need to change these permissions. We need full permissions for all users as well as setting the Sticky Bit. The Stick Bit will allow the creator of files to delete their files, but no one else (except root users with elevated privileges).
sudo chmod 1777 /linux
The first '1' is the Sticky Bit'. The first '7' allows 'read', 'write', and 'execute' for the owner. The second '7' is for the groups that are set for the folder. The last '7' is for everyone else.
Switch into the new folder, 'cd /linux'. Use an editor, like 'vim' or 'nano', to create a file called 'test.txt'. Add some simple text to the file and save it. If you run the command 'ls -l', you should see something similar to Figure 2.
FIGURE 2
You can see in Figure 2 that I am the owner as well as my group has the ownership. So, my user and group can 'read' and 'write' to the file, but everyone else can only 'read'. Only my account can delete the file with 'write' permission.
We now have the folder set to share, we just need to get the folder into Samba so the service knows it exists and allows access to it.
Configure Samba
To add our folder to the share list, we need to edit '/etc/samba/smb.conf'. At the bottom of the configuration file, you can add new shares. The syntax is as follows:
[shared-name]
path=/path/to/shared/folder
writeable=yes
In our case, the section would be:
[share]
path=/linux
writeable=yes
In this case, the folder is '/linux' and the share name is 'share'. The two can be the same if you want it to be.
You can test the syntax of the 'smb.conf' file by running 'testparm'. You may notice that when it displays the line 'writeable=yes' as 'read only=no'. These lines are the same, but it does not change the line in the configuration file.
Now you need to restart the 'smb' or 'smbd' service using 'systemctl'.
sudo systemctl restart <service-name>
Under normal circumstances, no SELinux, this should be enough. Let's have a look at the share.
Samba Client
We need to set up a new user for Samba to allow the client to connect. We are also setting up the account on the local machine (Server1). The command is:
sudo smbpasswd -L -a <username>
So, on my system, I used the command:
sudo smbpasswd -L -a jarret
The parameter '-L' is for the local system and '-a' is to add a user.
You might be asked for the password to use 'sudo' and then for the command, you'll be asked to create a password and then retype it to verify that the two entries match.
To log into the system and connect to 'share', use the command 'smbclient //localhost/share'. It should ask you for the Samba password of the current user. If you want to log in as a different user, then use '--user=<username>'.
Once connected and logged in, you can use Samba commands at the 'smb: \>' prompt. You can use 'ls' and 'pwd' as you would in Linux.
NOTE: Everything should be working fine on Ubuntu since it defaults to permissive mode. You can change the default in the file '/etc/selinux/config'. On the line 'SELINUX=permissive', change it to 'SELINUX=enforcing', save the file, and restart the system. If you do, Samba will stop sharing the file. To make it work, you need to perform the same commands as in CentOS or leave it as 'permissive'. Setting Ubuntu as 'enforcing' can cause it not to work in VBox. To fix it, you need to go back into Recovery mode and edit the file, changing it back to 'permissive'.
So, let's assume that Ubuntu is in 'enforcing' mode like CentOS and we get an error using 'ls'. We can use 'pwd' to get the current folder name.
Since the folder will be a Samba share, we need to change the context type. If you run the command 'ls -dZ /linux' to see the directory (-d) and context (-Z) of the shared folder. The result is shown in Figure 3.
FIGURE 3
You should see the user is 'unconfined', the role is set to 'object_r', and the type is 'default_t'. We need to change the type to 'samba_share_t' so SELinux will recognize the folder as a Samba share. Use the following command to change the type on the share:
chcon -t samba_share_t /linux
You can run the 'ls -dZ /linux' command to see that the type has changed. If you use the 'restorecon' command, the type is set back to default and the share is lost.
If you connect to the smbclient, then you can run 'ls' and use the 'get' command to copy the file to the 'pwd' on your system. That is the 'pwd' before you run the 'smbclient' command'. The 'ls' command is shown in Figure 4.
FIGURE 4
Permissive Service
If you run the command 'seinfo --permissive', the result is 'Permissive Types: 0'. We have no service set as Permissive.
We can use 'restorecon' to set the share back to 'default_t'. The command is 'sudo restorecon -Rv /linux'.
The Samba share should not be functioning again. So let's enable the Samba service as 'permissive'.
Use the command 'sudo semanage permissive -a smbd_t'. We specify 'smbd' as the service and '_t' as the type.
The SELinux policies should be recompiled after you issue the commands.
You can use 'ls' after connecting to the share and it should work.
Using the command 'seinfo --permissive' shows that there is one service and it is listed as 'smbd_t'.
Remote Connections
To allow connections to the local share from remote systems, you need to allow port access to TCP Port 445 and profile 'dns'.
sudo ufw allow dns
sudo ufw allow 445/tcp
On clients, you need to install the 'smbclient' for access from the command line. Otherwise, you can use 'nautilus' to open up the share from 'Other Locations' and then the Server and the share.
Conclusion
There was a bit of information here to set up security. Be sure to know this before you take the exam, if you do.
Try setting up SELinux with other services to make sure you understand the concept.

