After allowing the new kernel update (5.15.0-82-generic)
and rebooting the display on the screen appeared and reappeared, flickering
repeatedly.
This performance appeared after a reboot of the new kernel and after I walked away and Mint generated the black screen after no use that I had it set to. Upon moving the mouse to wake the system up that's when the flickering began and the system was unstable/unresponsive.
Dropping to a shell and running sudo shutdown -h now didn't work. The command failed and bash produced "Expanded Security Maintenance wasn't enabled".
Curious I ran: 'apt list --upgradable' to see what was available.
This entailed and pointed to Intel Microcode. I don't have and Intel tech on this rig:-
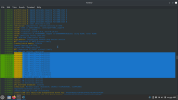
The dmesg log shows apparmor as being denied:-
I'm not an expert with the dmesg log. There's a lot of output in that log so it could be something else. IDK.
There are a handful of entries for patches to the microcode and one update for the microcode driver.
See the file attached:-
Hopefully it's not a kernel bug or a Wayland or X11 driver issue. I'll be back to see what you guys think of this.
I hope I can walk away, fire up the grill and when I come back to move the mouse this doesn't become a repeat.
and rebooting the display on the screen appeared and reappeared, flickering
repeatedly.
This performance appeared after a reboot of the new kernel and after I walked away and Mint generated the black screen after no use that I had it set to. Upon moving the mouse to wake the system up that's when the flickering began and the system was unstable/unresponsive.
Dropping to a shell and running sudo shutdown -h now didn't work. The command failed and bash produced "Expanded Security Maintenance wasn't enabled".
Curious I ran: 'apt list --upgradable' to see what was available.
This entailed and pointed to Intel Microcode. I don't have and Intel tech on this rig:-
The dmesg log shows apparmor as being denied:-
I'm not an expert with the dmesg log. There's a lot of output in that log so it could be something else. IDK.
Code:
ZFS: Loaded module v2.1.5-1ubuntu6~22.04.1, ZFS pool version 5000, ZFS filesystem version 5
[ 6.321536] audit: type=1400 audit(1693236010.431:2): apparmor="STATUS" operation="profile_load" profile="unconfined" name="libreoffice-senddoc" pid=798 comm="apparmor_parser"
[ 6.321708] audit: type=1400 audit(1693236010.431:3): apparmor="STATUS" operation="profile_load" profile="unconfined" name="libreoffice-xpdfimport" pid=800 comm="apparmor_parser"
[ 6.322360] audit: type=1400 audit(1693236010.431:4): apparmor="STATUS" operation="profile_load" profile="unconfined" name="/usr/bin/man" pid=794 comm="apparmor_parser"
[ 6.322363] audit: type=1400 audit(1693236010.431:5): apparmor="STATUS" operation="profile_load" profile="unconfined" name="man_filter" pid=794 comm="apparmor_parser"
[ 6.322365] audit: type=1400 audit(1693236010.431:6): apparmor="STATUS" operation="profile_load" profile="unconfined" name="man_groff" pid=794 comm="apparmor_parser"
[ 6.322519] audit: type=1400 audit(1693236010.431:7): apparmor="STATUS" operation="profile_load" profile="unconfined" name="lsb_release" pid=790 comm="apparmor_parser"
[ 6.322567] audit: type=1400 audit(1693236010.431:8): apparmor="STATUS" operation="profile_load" profile="unconfined" name="nvidia_modprobe" pid=791 comm="apparmor_parser"
[ 6.322571] audit: type=1400 audit(1693236010.431:9): apparmor="STATUS" operation="profile_load" profile="unconfined" name="nvidia_modprobe//kmod" pid=791 comm="apparmor_parser"
[ 6.322806] audit: type=1400 audit(1693236010.431:10): apparmor="STATUS" operation="profile_load" profile="unconfined" name="libreoffice-oosplash" pid=797 comm="apparmor_parser"
[ 6.325396] audit: type=1400 audit(1693236010.435:11): apparmor="STATUS" operation="profile_load" profile="unconfined" name="/usr/bin/redshift" pid=795 comm="apparmor_parser"
[ 95.921701] Bluetooth: BNEP (Ethernet Emulation) ver 1.3
[ 95.921705] Bluetooth: BNEP filters: protocol multicast
[ 95.921710] Bluetooth: BNEP socket layer initialized
[ 95.924955] NET: Registered PF_ALG protocol family
[ 95.939298] kauditd_printk_skb: 18 callbacks suppressed
[ 95.939301] audit: type=1400 audit(1693236100.047:30): apparmor="DENIED" operation="capable" profile="/usr/sbin/cupsd" pid=938 comm="cupsd" capability=12 capname="net_admin"
[ 96.020227] Generic FE-GE Realtek PHY r8169-0-500:00: attached PHY driver (mii_bus:phy_addr=r8169-0-500:00, irq=MAC)
[ 96.224341] r8169 0000:05:00.0 enp5s0: Link is Down
[ 97.776401] Bluetooth: RFCOMM TTY layer initialized
[ 97.776407] Bluetooth: RFCOMM socket layer initialized
[ 97.776410] Bluetooth: RFCOMM ver 1.11
[ 99.729002] wlp4s0: authenticate with dc:bf:e9:fd:39:ea
[ 99.730108] wlp4s0: send auth to dc:bf:e9:fd:39:ea (try 1/3)
[ 99.826451] wlp4s0: authenticated
[ 99.828223] wlp4s0: associate with dc:bf:e9:fd:39:ea (try 1/3)
[ 99.832147] wlp4s0: RX AssocResp from dc:bf:e9:fd:39:ea (capab=0x1411 status=0 aid=2)
[ 99.835647] wlp4s0: associated
[ 100.088889] IPv6: ADDRCONF(NETDEV_CHANGE): wlp4s0: link becomes ready
[ 103.455177] audit: type=1400 audit(1693236107.563:31): apparmor="DENIED" operation="capable" profile="/usr/sbin/cups-browsed" pid=1208 comm="cups-browsed" capability=23 capname="sys_There are a handful of entries for patches to the microcode and one update for the microcode driver.
See the file attached:-
Hopefully it's not a kernel bug or a Wayland or X11 driver issue. I'll be back to see what you guys think of this.
I hope I can walk away, fire up the grill and when I come back to move the mouse this doesn't become a repeat.
Attachments
Last edited: