I am trying to configure MFA on an a domain joined amazon Linux instance through Radius to LinOTP.
I have managed AD, Radius and LinOTP configured and working properlyI followed this documentation to configure the LinOTP and Radius: https://aws.amazon.com/blogs/desktop-and-application-streaming/integrating-freeradius-mfa-with-amazon-workspaces/ I used this to join linux instance to domain:https://docs.aws.amazon.com/directoryservice/latest/admin-guide/join_linux_instance.html
On the linux instance i downloaded PAM_Radiushttps://github.com/FreeRADIUS/pam_radius
Here are the configuration on the linux:
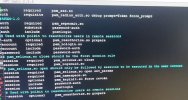
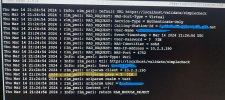
I added the details of the radius server in the /etc/pam_radius.conf file
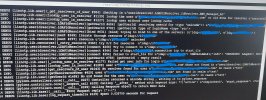
The content of the etc/pam.d/sshd file is attached
The highlight of the /etc/ssh/sshd_config is:
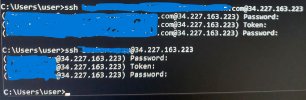
My problem is when I SSH to the Linux instance, It asks for a password. After I enter my domain password, It asks for the OTP Token and then it goes back to asking for password and so on.
sign in method 1: (FQDN) I ssh to the instance using: ssh [email protected] @<public Ip address>
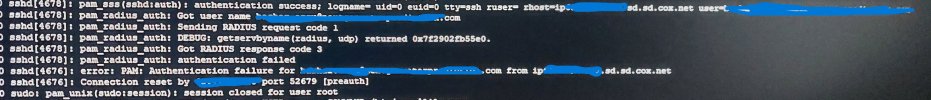
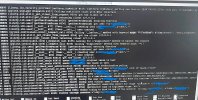
Here is what I see in logs:
sign in method 2: (without FQDN)I ssh to the instance using:ssh username@<public Ip address>
Here is what I see in logs:
I need some guidance on how to configure this amazon linux instance using domain credientials to authenticate to managed AD then use OTP(through radius and LinOTP) to do MFA. I appreciate your guidance. I attached some snapshots of configuration and logs that might help troubleshoot the issue. look at filename for description
I have managed AD, Radius and LinOTP configured and working properlyI followed this documentation to configure the LinOTP and Radius: https://aws.amazon.com/blogs/desktop-and-application-streaming/integrating-freeradius-mfa-with-amazon-workspaces/ I used this to join linux instance to domain:https://docs.aws.amazon.com/directoryservice/latest/admin-guide/join_linux_instance.html
On the linux instance i downloaded PAM_Radiushttps://github.com/FreeRADIUS/pam_radius
Here are the configuration on the linux:
I added the details of the radius server in the /etc/pam_radius.conf file
The content of the etc/pam.d/sshd file is attached
The highlight of the /etc/ssh/sshd_config is:
- passwordauthentication yes
- challengeresponseauthentication yes
- usepam yes
My problem is when I SSH to the Linux instance, It asks for a password. After I enter my domain password, It asks for the OTP Token and then it goes back to asking for password and so on.
sign in method 1: (FQDN) I ssh to the instance using: ssh [email protected] @<public Ip address>
Here is what I see in logs:
- Linux instance: /var/log/secure
- authentication success
- LinOTP: username not found in realm
- When I look at the radius logs, it seems that the OTP password is not correct since the field user
sign in method 2: (without FQDN)I ssh to the instance using:ssh username@<public Ip address>
Here is what I see in logs:
- Linux instance: /var/log/secure
- invalid user username
- LinOTP: found username
- When I look at the radius logs, it seems that the OTP password is not correct since the field user
I need some guidance on how to configure this amazon linux instance using domain credientials to authenticate to managed AD then use OTP(through radius and LinOTP) to do MFA. I appreciate your guidance. I attached some snapshots of configuration and logs that might help troubleshoot the issue. look at filename for description
Attachments
Last edited by a moderator: